Tushar Mehta / Android Authority
Google is set to change, if not completely eradicate, Android sideloading as we know it. The change comes into effect as early as September this year, and could make sideloading more drawn-out and cumbersome.
While Google has ensured sideloading isn’t going away, it plans to introduce a “high-friction” flow for installing apps from unverified developers. This is certain to unsettle many people, especially power users. But for the broader Android user base, it could be a lifesaver, especially with APK-based attacks on the rise.
While sideloading has been the most beautiful and liberating aspect of Android, it’s heading for a watershed moment. And here’s why embracing it, rather than opposing it, could ensure Android lives longer.
What do you feel about Google’s plan to limit sideloading on Android?
22 votes
A case for making sideloading on Android slower by design
One of the primary reasons to crack down on unverified installations on Android is the substantial increase in APK-based malware attacks over the years. Kaspersky alone identified more than 22 million potential incidents of attacks on Android users in the first half of 2025, a notable 29% increase compared to H1 2024. The report cited nearly 143,000 different strains of infected app packages, or APKs, distributed through seemingly harmless channels. A third of these packages were designed for banking fraud.
In addition to Kaspersky, organizations such as Malwarebytes and Zimperium have noted instances in which attackers prey on human vulnerabilities or temptations to distribute malware. These malicious apps masquerade as modified versions of otherwise free apps and are distributed through Telegram, Discord, and other unregulated social channels. The best part? These apps even work as promised, so they don’t make the user suspicious immediately.
Besides modified apps with perks, attackers also use garbs of free tools or apps with adult content to lure users into installing them. Often, these apps, especially when downloaded from unreliable sources or via messaging channels, include an embedded software development kit (SDK) that can be used to install a remote access tool and subsequently take over a user’s phone, with the ultimate goal of emptying their bank accounts.
APK-based attacks have evolved, and so should Android.
You would rightly think that if someone is foolish enough to download a “modified” Netflix or Spotify to access content for free and without ads, they deserve to be tricked. But that’s unfortunately not the only means attackers use to target tech-averse users. One of the common means to distribute malicious APKs is through WhatsApp or other similar instant messaging platforms.
One of the common MOs that has emerged since 2025 in parts of Eastern Europe and Asia is sending fake wedding invitations or traffic fines. Another popular technique is to distribute imposter apps that pretend to be the same as popular ones, such as Chrome or WhatsApp, or even impersonate bank apps.
And with AI coding agents now whipping out (or should I say, “vibe-whipping” out?) apps faster at a breakneck speed, the dangers are only going to increase for users who can’t immediately tell the difference between real and fake apps. These more recent attack vectors, especially those that use messaging or other social media app distribution, easily evade caution for unaware users. A “wedding invitation.apk” only guarantees free booze and food after all, doesn’t it?
The increase in sophisticated and novel attacks on Android users mandates intervention from Google, and here’s what it proposes to do.
Sideloading stays — at least for now
Mishaal Rahman / Android Authority
When Google first announced plans to restrict sideloading APKs, it was immediately met with resistance from users. The reaction was obvious, given that sideloading has been one of the most fundamental traits that signify Android’s openness.
Google approached this by targeting scammers that “rely on anonymity to scale their attacks,” in the words of Android Ecosystem president Sameer Samat. So, Google said it would start requiring developers to be identified and verified, even if they do not distribute apps through the Play Store. The objective was to add a layer of accountability for developers, but it also resulted in concerns echoed by developers who deliver apps that lie in the gray area. A significant example is console emulation, where emulator apps themselves might be legit, but the ROMs or the game content being used with those apps may be distributed without proper permissions from the game publishers.
Google has eased its restrictions to accommodate power users. Will that protect the others?
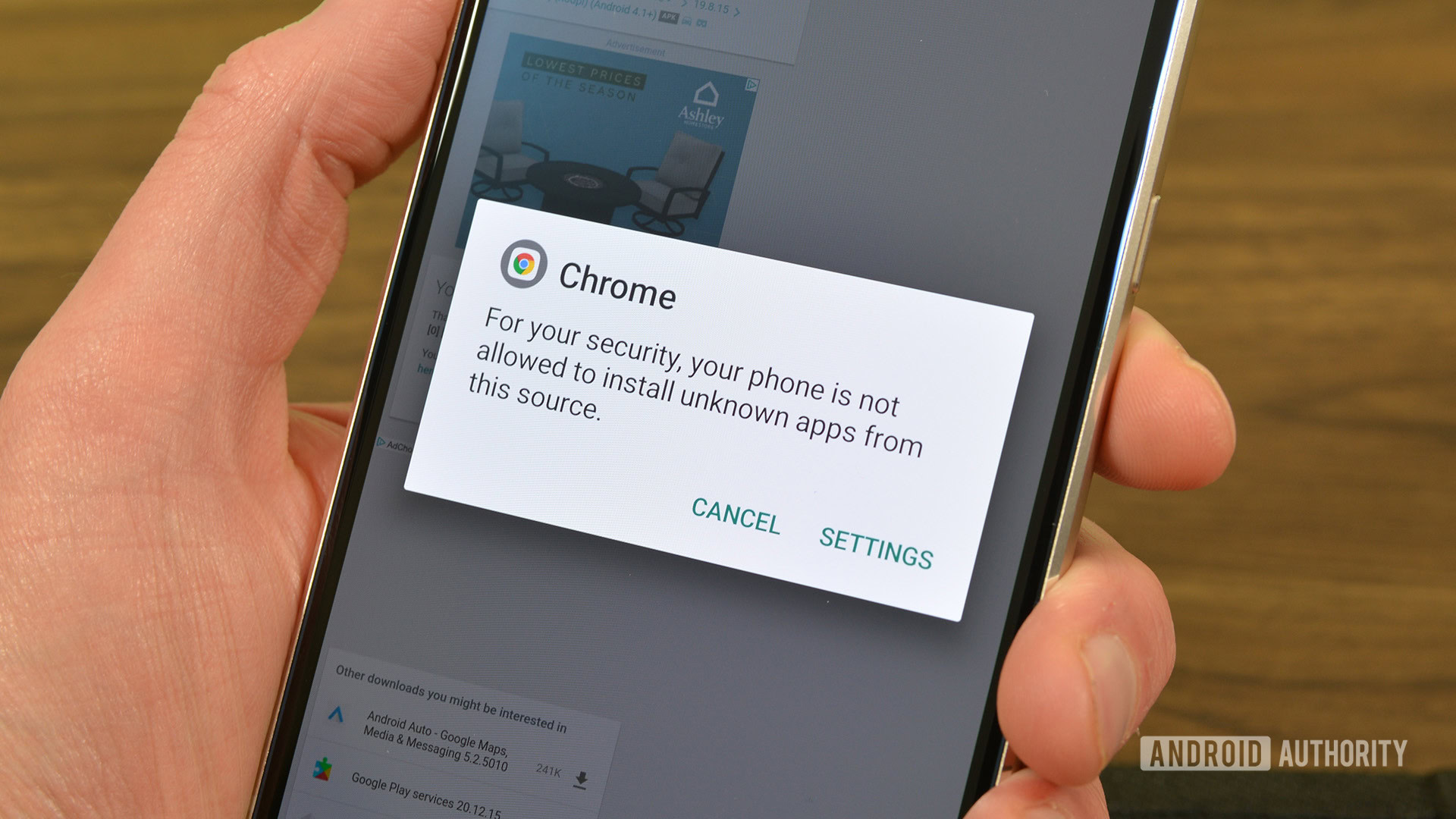
However, with the criticism that followed, Google lowered its guard and said it would allow users to install apps, even from unverified developers, but with some caution. The flow, by the way, would look a lot different and more seamless in cases of verified third-party stores (thanks to Epic’s persistence against Google). Thankfully, it does not completely block users from sideloading apps. It just warns them more intensely.
More recently, we spotted the exact wording of what could be a cautionary message when users try to install apps from developers not registered with Google, reminding them that their “devices would be at risk.” Matthew Forsyth, Director of Product Management, Google Play Developer Experience & Chief Product Explainer, even confirmed that this won’t be a restricting situation but an intended “high-friction” flow.
A high-friction flow feels like the necessary evil for millions, even billions, of the vulnerable users.
If you’re an experienced Android user, it shouldn’t stop you from installing an app. On the contrary, a novice or a less technologically inclined user, like my 65-year-old dad, would probably feel deterred or at least warned before they unknowingly tap a few buttons to install an app. As much as I hate that generalization, it’s also true for the majority of users who are either too old or too young.
While the approach does not safeguard users from just continuing to tap without reading error messages on the screen, this is better than the current latchkey kid situation we have in Android currently. More importantly, it prevents Android from becoming the walled garden that we’ve abhorred Apple and its app ecosystem to be for all these years.
And it can’t be any more annoying than Android’s existing restrictions for installing apps from unknown sources.
Not the best option, but not the worst one either
There’s no skirting around the truth that Google’s insistence on verifying developers, or otherwise slowing down users while they sideload apps, is hurtful to the spirit of freeness. But it also feels like a necessary evil. Despite its benefits, sideloading can unfortunately no longer be limited to a “power user move,” and Google’s tightening of the process could also be viewed as a reckoning in the face of adversity and the sheer increase in the volume of attacks on Android users.
Android remains a garden without walls, but with vital barricading.
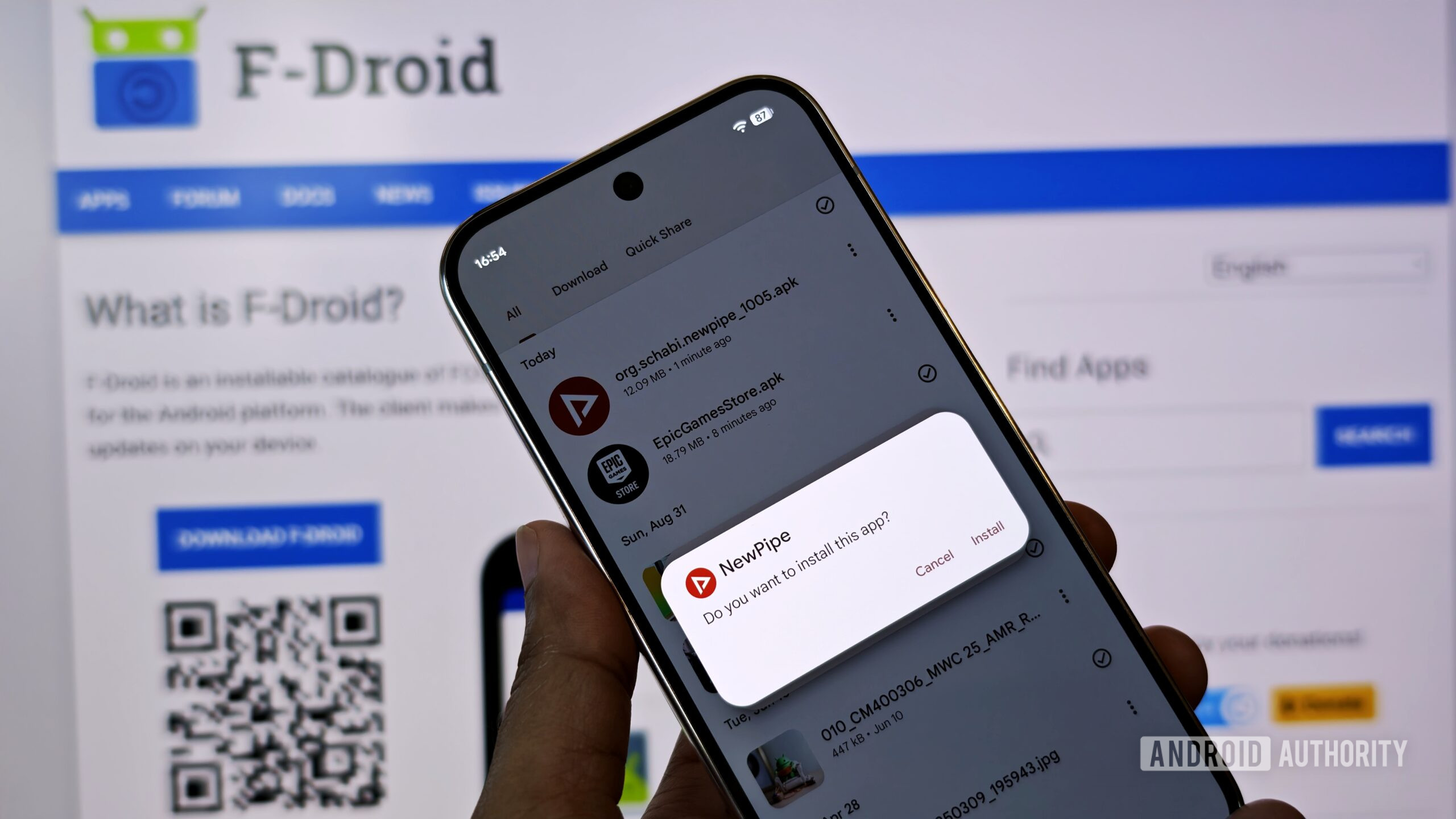
As we progress, it might be precious, for Google and for us as users, to evaluate how to balance the risks and benefits of certain apps. While we can trust peer-reviewed open source apps in F-Droid or an exciting project from a student developer, we would need to be wary of downloading apps from murky GitHub projects, and warnings that Google plans to implement may help — “may” being the keyword here.
While it’s difficult to ensure the effectiveness of this solution, I feel it is better that users are warned and inconvenienced than robbed.
Thank you for being part of our community. Read our Comment Policy before posting.





